Guide from Hacken: How to choose a secure yield farming platform?

The quest for the best yield farming platform is underway. You have already studied the light papers and know the average APYs across the market. The next big step is to look into security. So many questions. Where to start, and what’s essential? How to calculate the risks? Where to get objective data? How long would it take?
With a little bit of expert help, you can easily perform your own accurate and time-efficient Due Diligence to get ahead of the curve.
We teamed up with a leading blockchain cybersecurity company Hacken to get the answers. We chose Hacken because they are industry experts in smart contract audits and know everything about blockchain security. CoinMarketCap and CoinGecko recognize Hacken’s audit reports, which speaks volumes about their industry recognition. Hacken is at the forefront of industry-wide smart contract audit standards as they are one of the contributors to EthTrust Specification. With five years of experience, 180 partners, and more than 1,000 protected clients, Hacken is among the top blockchain security auditors.
Here’s a step-by-step guide from Hacken’s cybersecurity experts on how to choose the most secure platform for yield farming.
Step 1. Check Scope and Relevance of Smart Contract Audit
It’s impossible to overestimate the importance of smart contracts for yield farming platforms. A Smart contract is a code that governs and automates transactions. It typically consists of multiple functions, such as staking, withdrawing, lending, etc., that power up a DeFi platform’s operations.
Secure smart contracts work as intended every time without any loophole for manipulation. Unfortunately, smart contracts are rarely without vulnerabilities.
The most common are:
- Reentrancy
- Oracle Manipulation
- Over and underflows
- Frontrunning
- Timestamp Dependence
- Denial of Service
- Griefing, and Force Feeding
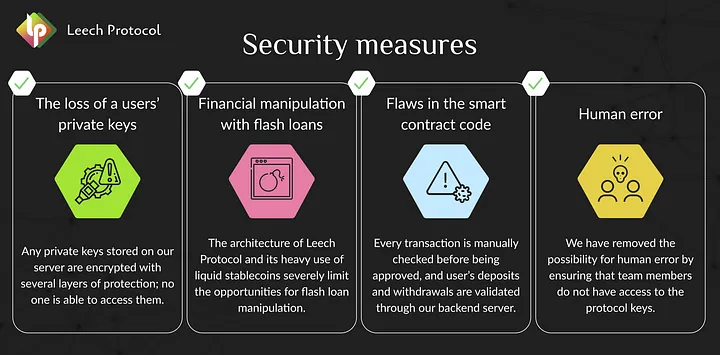
All these vulnerabilities enable data breaches or private key leaks. The good news is that yield farming platforms can address these vulnerabilities with an external audit. An external audit is basically a thorough code review to ensure that all functions of the smart contract code work as intended without any hidden loopholes. Writing perfect code is almost impossible because developers are only humans who occasionally make errors. This is especially true when devs are constrained by time and resources.
Smart contracts are vital for secure yielding platforms, but not all audits are created equal. Relevance and coverage are two main questions you must consider. The audit must be relevant and cover the entire project. Web3 projects typically have multiple smart contracts to ensure all of their features work as intended. All contracts (not just one) must be audited.
- Check the number of smart contracts vs. the number of audited smart contracts. Be cautious if the share of audited contracts is significantly low.
- Check for relevancy. The deployed code should perfectly match the code that was audited. Any major alternation between the two is a valid reason for caution.
Checking audit relevancy and scope with an example
Step 1. Locate Public Audit
Let’s take a look at one of Hacken’s clients, Zharta — a lending platform. Notice “Auidited by Hacken” badge on their website.
Conveniently, Hacken website provides a list of all the public audits it has completed. We can easily locate Zharta’s audit here.
Step 2. Locate a codebase repository
First, let’s head to the “Scope” section on Page 4. We have a link to the repository and commit. The repository here matches the codebase that Hacken audited.
Step 3. Check audit relevancy
Once in their GitHub repository, notice the date of the last commit for ./protocol-v1/contracts/ (highlighted in red).
The date of the last commit matches the date of Hacken’s audit. As a result, the audit is 100% relevant (as of the day of writing).
Step 4. Check audit scope
Inside the same folder (protocol-v1/contracts/), we have counted the number of key files — 12 smart contracts in the Vyper programming language. Inside the protocol-v1/interfaces folder, we count 11 contracts.
Noooow, let’s compare this number with what’s inside the audit report. Go to Hacken’s audit report once again, and locate the Audit Scope section for the Fourth review scope.
The audit by Hacken reviewed 12 contracts in the ./contracts folder and 11 contracts in the ./interfaces folder. Zharta’s codebase is powered by the same number of contracts. Therefore, the audit covers close to 100% of the key on-chain functionality.
Step 5. What about vulnerabilities?
It’s finally time to look at found issues inside the report. Hacken found 2 critical issues, 16 high, 5 medium, and 4 low. Three iterations later, Zharta developers resolved almost everything. You can read more about each found issue and how it was fixed in the report. Also, the final audit score is 8.4
It’s time for conclusions
- All high, medium, and critical issues have been fixed.
- Audit is relevant as the data of the last commit matches the date of the review.
- The audit covers all contracts in ./contracts and .interfaces folders.
The Zharta landing platform has almost perfect audit coverage and relevancy with a very high score of 8.4. However, not all audits are this diligent. Unfortunately, we have hundreds of crypto projects with low coverage and a codebase that is no longer relevant.
Again you can check Audit Relevancy and Audit Scope metrics at CER.live, but not all projects are listed there yet.
Step 2. Is the Blockchain Protocol Safe?
A protocol audit is different from a smart contract audit. Yield aggregators can interact with one or more blockchains. Leech, for example, works across 12+ blockchains. Some chains, such as Ethereum or Avalanche, are well-established with minimal security concerns. New chains are less recognized and don’t enjoy the same level of trust. DefiLlama lists 290 yield farming protocols working across more than 50 chains in total.
You cannot assume that each one is safe. A new chain can earn trust by having an external blockchain audit. To verify whether a blockchain is audited, go to its website and check for the security page. Alternatively, information about the audit can be retrieved from the project’s repository on CoinGecko’s Security tab.
Step 3. Background Check
The significant purpose of a background check is to minimize the risk of a rug pull. Not all founders have the best intentions in mind. Some are growing their yield farming business with the sole goal of running off with users’ and investors’ assets. You’ll never see them again, and no one will return your money. Rug pulls happen almost monthly, so stay clear of fraudulent projects.
Reputation is everything in a trustless environment. Look for LinkedIn pages, video interviews, and other valuable information about the platform’s founders. Who are they? Are they DeFi experts with a proven track record or amateurs with risky ideas and no credibility? We understand that some projects are small, some don’t have enough media coverage, and some want to remain anonymous. For that reason, look at the platform’s closest partners, features in the media, and social media presence. Also, look at partners’ websites or resources for project mentions.
Having credible certification also helps. For example, our clients can display “Proofed by Hacken” Certification on their websites to prove they are a legitimate business that takes security seriously. CER.live, CoinGecko, and CoinMarketCap will also display cybersecurity information about the project.
Step 4. Look at Objective Cybersecurity Ratings
We encourage doing your own research, but you can rely on public resources to make your DD process more cost-effective. Don’t do the same work twice. There are trusted players on the market with the sole purpose of scrutinizing Web3 projects for security.
Go to CER.live, a free service offering the most objective security score for crypto projects. Find a detailed security breakdown of a yield platform of your interest. Type in the platform’s name, and you’re all set. Now, you get credible data on security rating, token audit, token audit relevance, platform audit, market cap, bug bounty, insurance, and prior incidents. CER.live independent researchers collect and verify dozens of security indicators to give investors this utility for free.
How trustworthy is CER.live? CoinGecko, the top data aggregator in the whole crypto world, relies on CER.live’s data for its Trust Score. CER.live cybersecurity score makes up 20% of the overall Trust Score on CoinGecko. Speaking of Trust Score, be sure to check it for your project. Moreover, anyone can look at how CER.live’s on-chain data researchers assign ratings thanks to a public evaluation methodology of cryptocurrencies with a complete scoring system.
What is the best platform for yield farming in terms of security?
The best crypto yield farming platform is the one that combines the highest APYs with the lowest yield farming risks.
Cybersecurity is a vital bottom line for any yield farming platform. High yields and outstanding features don’t matter when users lose funds to hackers. To outrun the market, you must think long-term and pay attention to security. As a possible alternative — you could lose money.
How do you lose money in yield farming? The answer is simple — you don’t care about Due Diligence.
Cybersecurity is paramount for yield farming platforms. In theory, yield farming should generate a substantial return on investment. In reality, crypto users risk losing everything due to painful hacks, exploits, or frauds. Hacken experts provided insights on choosing the most secure yield farming platform in four simple steps:
(1) cybersecurity ratings
(2) relevant and in-scope smart contract audits
(3) protocol audits
(4) founders’ background check.
These four steps make up the foundation of a winning risk assessment.
Also, when choosing farmings and vaults, remember the basics of investing in yield farming:
- Tokenomics of the yield farming platform. How does the project make money? A platform printing out tokens as a reward with no underlying revenue mechanism should raise eyebrows.
- What’s the share of algorithmic coins? Find out which tokens are used for farming, and keep in mind that algorithmic is the most dangerous type of stablecoin.
- What is the pool size and end date? Don’t be the last to enter, or else you’d lose on price impacts.
- Study entering and exiting. What are the chains and coins used for entering and exiting? Will you have trouble with liquidity? Are there any fees or asset freeze periods?
- Now, it’s time for a test run. When you’ve chosen a platform that satisfies your criteria, take $10 (or any sum you’re comfortable with) and check how everything works. A test run will, for example, help you see if the APY is displayed correctly. Sometimes, there’s a front-end error when displaying rewards per day.
Interested in this topic? Continue the conversation on Leech Protocol Discord.
Join Hacken in Discord for the latest news on Web3 cybersecurity.
What should you do next?
- Provide liquidity via our farming App
- Follow our Twitter for more DeFi and YieldFarming tips
- Join our Telegram for Daily Farming discussion
- Join our Discord to claim your roles and become an early community member